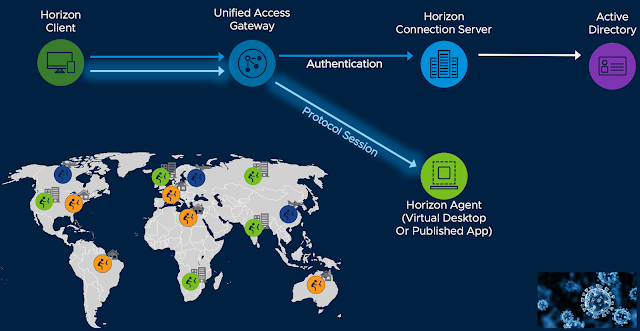
Folks considering a migration from Citrix to Horizon naturally ask, "what's the Horizon equivalent of NetScaler?" Though Unified Access Gateway (UAG) is the closest comparison, it's not a like-for-like equivalent to NetScaler. NetScaler is a multi-purpose application delivery controller, traditionally sold in pairs of physical appliances, with a history of solving complex problems far beyond the scope of Citrix remoting. In contrast, Horizon's UAG is a purpose built, exclusively software based technology dedicated to VMware EUC workloads and little else. So, while both solutions are used to proxy display protocol traffic for their respective suites, they're very different in scope and approach. That said, to compete with the broader set of NetScaler capabilities UAG combines with components across the entire VMware portfolio to provide a modular, elastic, and cost effective alternative.
To be clear, NetScaler is very impressive tech with a broad set of capabilities extending far beyond app and windows remoting. Load balancing, GSLB, web security, TCP offloading, etc... The common refrain is, "NetScaler does everything." The problem is NetScaler does everything and is priced accordingly, despite the fact most Citrix customers need it simply to proxy ICA sessions. Usually these organizations have some other load balancing or ADC solution in place and quite often you hear of NetScalers sitting in the same racks as F5 appliances. Unfortunately, NetScalers dedicated exclusively to the proxying of ICA sessions is an extremely common scenario, overkill most Citrix customers find themselves forced into as soon as remote access is required. A colleague of mine jokes it's like having a Ferrari to drive 35mph for three blocks to a local market once a week. In stark contrast stands Unified Access Gateway, a standard component of all VMware EUC suites, deployed at no additional cost, save the modest vSphere capacity used to run it. While it already had proven itself by 2019, it's stellar performance during the pandemic cemented it's status as a hardened and mature solution.Infrastructure As Code
UAG was first released 8 years ago as an alternative to the Windows based Horizon proxy solution called Horizon Security Server. As opposed to it predecessor, UAG is a hardened linux virtual appliance currently based on photon OS 3.0. It's typically deployed on top of vSphere, though it's also deployed natively to clouds like AWS, Azure and GCP. Over the years it's role has expanded to accommodate Workspace ONE UEM solutions like Per-App VPN and SEG. Throughout the course of it's development security and stability have been a top priority, a fact quickly evident to anyone who's worked with the product. Quite frankly, these things don't really break. Most of the troubleshooting happens during initial setup and easily 95% of the time problems are with external environmental factors like misconfigured firewalls or general networking challenges. Once UAGs are setup properly they just work and don't require much in the way of care, feeding, or maintenance. With the release of Horizon 8 in 2020 UAG became the primary mechanism for supporting remote Horizon access as Security Server was deprecated. By then, there was already tens of thousands of successfully deployed UAG instances, along with a rich set of documentation and codified best practices. In short, UAG is boring, reliable, proven and predictable plumbing used by VMware's EUC solutions to provide secure access to on-premises resources.
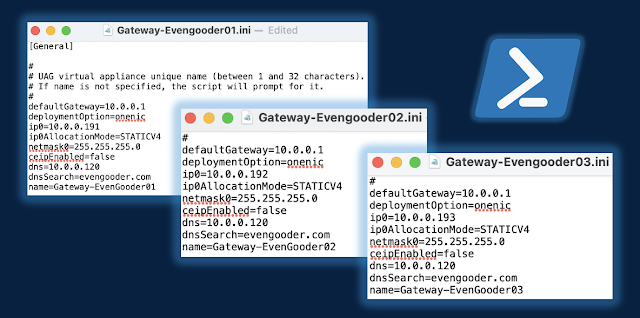
While security and reliability were top developmental objectives for UAG, ease of deployment was certainly lower down on the list of priorities. Typically, mature environments entail the deployment of UAGs through PoweShell scripts run against vSphere. This can be initially off-putting for folks, given network infrastructure specialist normally don't get their hands dirty with scripting. However, while you're running a pre-canned PowerShell script provided by VMware, you're not actually writing or tweaking out PowerShell. You're focus is on tweaking out an ini config file that the PowerShell script is run against, populating the ini file with info about your UAG instance like ip addresses, gateway and Horizon configurations. Once you get a working config you end up with an easily repeatable and tweakable deployment process that typically takes about 3 minutes to stand up a new a completely functional UAG instance. It's very much in the spirt of infrastructure as code, providing complete transparency. We're not talking about standing up a physical device, giving it an adorable name, and marveling at it's mysterious and obscure workings. We know how these UAG instances work. It's spelled out clearly in an ini file that's reliably leveraged throughout various instantiations and upgrades.
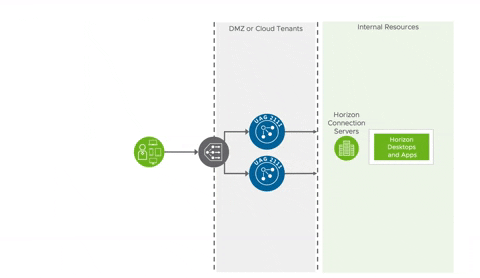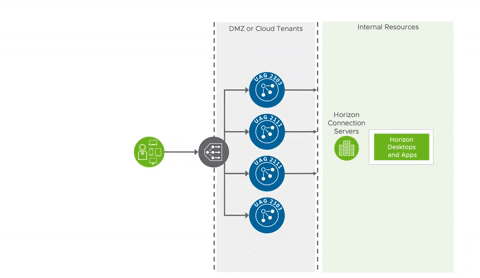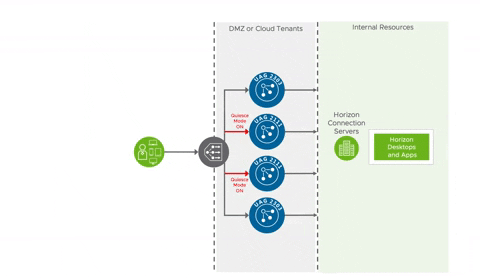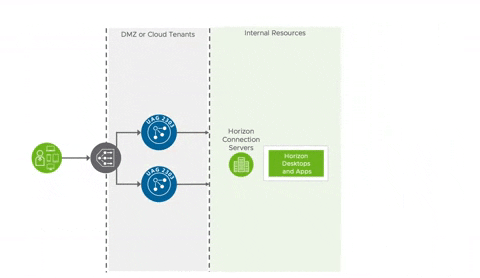
The first steps for most customers is to initially deploy a UAG appliance using an OVF wizard through vSphere, then fine tune the appliance configuration through it's web interface. Once they have a working instance setup, they export the configuration settings from the web interface, and voila, a working, reusable ini based config is available for redeployments, updates and scaling. Backups of a specific UAG instance amounts to one of these ini files, certificates, and standard downloaded .ova for the specific appliance version. Line these three resources up on a command line, and you're good to go with a redeploy in 3 minutes. Tweak out names of the appliance and ip address, and you've got your 2nd, 3rd, 4th, or 5th UAG in the works. With each UAG handling up to 2K sessions, logically you're entire UAG deployment adds up to a handful of ini's, certificates and downloaded .ova files. Upgrades amount to downloading a new .ova, tweaking out the the .ova path of your ini's and redeploying through PowerShell. New UAG instances are spun up behind the load balancer, while older versions are placed in a special Quiesce Mode as they're slowly drained of sessions and eventually decommissioned. All of this can occur with zero downtime.
When you get a process like this in place you get machine like reliability that rarely falters outside of environmental disruptions from dependencies like load balancers, ssl certs or the network. In a nutshell, supporting infrastructures typically wears out before the UAG's do. If there is a challenge suspected with the UAG instance itself, one of the first troubleshooting steps is to redeploy. With UAG deployments being repeatable and largely uneventful affairs, redeploys are commonly leveraged both for migrations to newer versions and troubleshooting purposes. This shift to a fluid, infrastructure as code, model is daunting at first, but with some planning and elbow grease, yields a reliable and transparent remote access solution that leverages and benefits from vSphere infrastructure. Backups are a piece of cake, upgrades are non events and replicating deployments for new environments is straight forward. Generally speaking, if something breaks, it's usually cause someone has done something stupid with a dependency. (Can you tell I love this solution? I do. Don't even get me talking about it when I'm drunk. I'll call it folksy and blue collar, sexy and a little bit edgy.)
Meeting Load Balancing Requirements For UAG
In typical deployments UAGs are placed within a DMZ between firewalls and 3rd party load balancers. Along with enabling redundancy load balancers are key to the zero down time upgrades described in the previous section. When comparing UAGs to NetScaler this requirement for external load balancing is one of the most common features gaps called out. Fortunately, you can use one of the gazillion load balancers in existence to address this challenge. Most customers I've interacted with have enterprise grade load balancers in place long before Horizon enters the picture. Fortunately, load balancing requirements for UAG are straight forward and, to date, I've never come across a situation where an enterprises grade solution wasn't able to accommodate UAG. The requirements are clearly spelled out in the article, Load Balancing Unified Access Gateway For Horizon. Further, many vendors have their own processes specifically documented, such as this article from F5. There's even solid guidance on leveraging NetScaler's load balancing capabilities for UAG, such as this article from the venerable Carl Stalhood.
All that said, if you're looking for a new load balancing solution VMware's is more than happy to sell you a software defined load balancing solution called NSX Advanced Load Balancer, what used to be called Avi Vantage. It enables elastic scaling and provisioning of load balancing functionality through service engines that are spun up and down across vSphere and native hyperscaler environments, with a software based Avi Controller centralizing control and management. When it comes to standard load balancing or global load balancing, it's competitive with any other load balancing solution you might run across, including NetScaler. Most notably, it's incredibly cost effective, enabling agile right sizing of load balancing capacity across vSphere and cloud environments, mirroring the agility offered through UAG. It's a compelling alternative to traditional hardware based load balancing solutions, so much so that NetScaler felt threatened enough to try and sue Avi out of existence back in 2017, a law suit that was eventually settled. For a more in depth primer on NSX Advanced Load Balancers, check out this article I wrote in 2020. Further, as with many other load balancing vendors, there's UAG specific load balancing guidance provided in the article, NSX Advanced Load Balancer for Load Balancing UAG Servers. 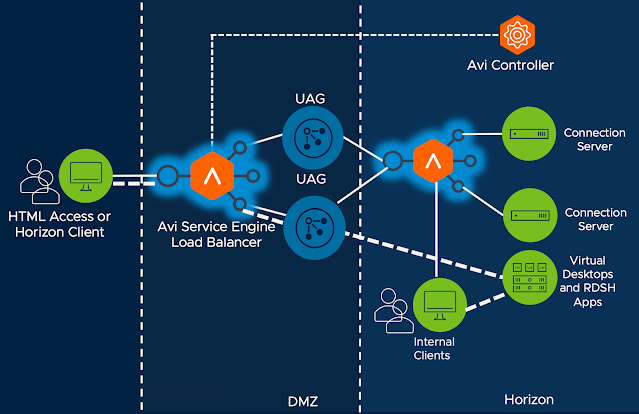
Finally, while NSX Advanced Load Balancer and many other 3rd party solutions provide global server load balancing (GSLB), if your GSLB requirements are limited to Horizon there's a purposed built SaaS solution called Universal Broker. It works by leveraging the cloud based Horizon Control plane for authentication and intelligent routing of sessions across separate Horizon PODs. Horizon protocol traffic is bifurcated, with the primary protocol working against a cloud based URL and display protocol traffic traversing UAG appliances. Universal Broker is part of a larger initiative to enhance Horizon environments with cloud based services. While it isn't for everyone, it's a beautiful example of VMware offering a SaaS based alternative for functionality traditional delivered on-premises. For more information, check out this primer on Universal Broker, The Innovation And Current Limitations Of VMware's Universal Broker For Horizon.

Honestly, I don't hold much allegiance to any load balancing solution when it comes to designing Horizon environments. Quite frankly, for Horizon deployments I conceive of load balancers as a commodity, with the selection of vendor preordained by whatever solution customers already have in place. Though it's critical to get load balancing setup properly, there's not a lot of room for creativity or differentiation in terms of Horizon outcomes. It's more science than art.
Stronger Forms Of Authentication For Horizon Remote Access
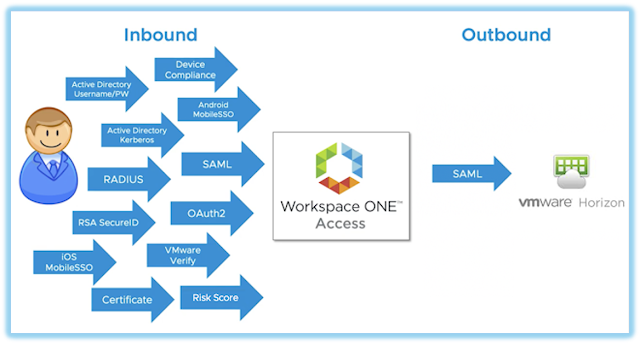
Passthrough is the default authentication method for UAG deployments. Via the primary Horizon protocol, prior to the display protocol connection, AD credentials are passed through the UAG appliance onto the Horizon Connection servers, then executed against the AD environment the Connection server is joined to. While this is the default behavior, most organizations augment this security one way or another. For additional authentication from within the DMZ there's options for smart cards, certificates, RADIUS based solutions and RSA. There's also built-in support for OPSWAT endpoint compliance check. Historically, RADIUS based integrations with 3rd party MFA solutions have been very popular, allowing for simple integrations with solutions like Duo or Symantec VIP. However, over the last few years direct SAML based integrations with solutions like Okta, Ping and Azure have become more popular, with support for such integrations starting around 2019.
While direct integrations between UAG and 3rd party solutions are apt to get the job done, a more ideal method for accommodating stronger forms of authentication is through Workspace ONE Access. WS1 Access is like Storefront in that it provides a catalog, a simple grid of icons through a browser for folks to consume. However, WS1 Access also acts as an IDP and policy engine, enabling federation with popular SaaS solutions like like ServiceNow or Office 365, while also supporting integration with 3rd party MFA solutions. It's policy engine is leveraged to enforce contextual authentication requirements for Horizon, integrated Citrix environments, and any federated SaaS solutions. It's an ideal mechanism for wrapping modern authentication around Horizon environments enterprise wide, enforcing security policies when Horizon is consumed from the WS1 catalog or directly accessed through the Horizon client.
My favorite way to describe WS1 Access is that it acts as sort of an integration goo, allowing folks to leverage authentication solutions they already have in place. Through the WS1 Access Connector that's deployed on-premises AD environments are easily integrated with. Further, the connector has built in support for RSA and Duo, while allowing integrations to other 3rd party MFA solutions through RADIUS. The cloud based WS1 Access tenant itself can easily integrate with more modern MFA solutions provided by vendors like Okta, Ping and Azure through SAML federation, a very popular path forward nowadays. Most notably, for existing WS1 UEM customers, WS1 Access provides a built in integration allowing customer to extend WS1 UEM based security to Horizon access. This includes certificate based auth methods for Win10, macOS, iOS and Android, with an option to calibrate authentication requirements based on signals from underlying devices leveraging WS1 UEM's device compliance policies. In addition, WS1 UEM integration introduces an option to leverage VMware's own MFA solution Verify (Intelligent Hub). Finally, WS1 Access can drive it's contextual authentication policies bases on analytics from WS1 Intelligence like Login Risk scores or device risk scores. Big picture, as a policy engine, WS1 Access allows us to enforce different authentication methods based on the context of the users, enabling admins to calibrate and right size security based on user and device context. For more background on WS1 Access check out these intro and deep dive videos on Youtube put out by VMware's healthcare focused EUC team.
Through these policy based controls WS1 Access enables us to wrap Zero Trust security around legacy windows. Access to full desktops or individual published applications are firmly controlled and tracked through contextual access policies. To further this Zero Trust adoption, we can inform these controls with device posture information and analytics from both WS1 UEM and Intelligence. With such a deployment, Horizon is combined with Access, UEM, and Intelligence to create a superb remote access solution uncannily aligned with NIST Zero Trust guidance. This ideal model is easily achieved by layering SaaS based instances of Workspace ONE services on top of Horizon environments, starting with the SaaS based version of WS1 Access included with Horizon Universal licenses.
(NetScaler + UAG) In The Meantime Or Indefinitely
As mentioned earlier in this post, it's perfectly feasible to load balance UAG appliances with NetScaler. In fact, for many existing NetScaler customers it's an ideal and natural path forward. Quite often I hear the objection, "but I've already paid for these NetScalers and they're on a different renewal cycle than Citrix itself." Well, that's my kind of problem! The option to continue leveraging NetScaler appliances while migrating from Citrix to Horizon helps limit the scope of change during a major migration. Admins can focus on migrating the Citrix functionality itself without having to rip out load balancers or replace other NetScaler functionality at the same time, breaking down the overall transition into smaller bite size pieces. In the short term, continue leveraging NetScaler while adding load balancing support for UAG appliances. Chip away at your Citrix to Horizon migration first, then circle back later to replacing the NetScaler appliances if that's your eventual goal.
Or don't get rid of NetScaler at all. If you're happy with NetScaler and feel satisfied you're getting value out of it independently of proxying Citrix sessions, shoot, keep it. It's always possible your org is truly in need of a multi-purpose application delivery controller across the enterprise and NetScaler is fulfilling that function. Granted, that's usually not the case with my customers. Most of my customers are using NetScaler simply to proxy ICA sessions and maybe a little load balancing. Those organizations in particular should consider alternatives. However, if you are full-bore using advanced features of NetScaler across you entire enterprise and don't want to consider replacing this functionality AND you've made it this far through my article, heck, keep on keeping on. Treat Horizon and UAG as simply another solution to load balance and you're all good in the hood. In this situation, my best piece of advice would be to consider making the rest of the organization help flip the bill for the NetScaler functionality they're leveraging outside of Citrix remoting.