The foundational components for Zero Trust architectures such as MFA, ICAM and endpoint security are solutions widely deployed today. While most organizations already have these building blocks in place achieving Zero Trust objectives with their aggregate capabilities requires a level of orchestration and synchronicity that is far less common. In that regard, the integration and orchestration of a broad set of security components through a single platform, the Anywhere Workspace, is something VMware has been perfecting for over a decade now. To modernize legacy windows experiences Horizon is combined with Access, UEM, and Intelligence to create a superb remote access solution uncannily aligned with NIST Zero Trust guidance. Such a deployment meets the immediate need to optimize support for a hybrid workforce while establishing a beachhead for further Zero Trust adoption.
This post maps out Anywhere Workspace Zero Trust capabilities to guidance provided by NIST and it's subsequent work with the National Cybersecurity Center Of Excellence (NCCoE). The intent is to elevate a discussion about Horizon and Zero Trust by referencing a source respected and followed across the public and private sector. With federal agencies like CISA, DoD and the NSA paying deference to NIST guidance, along with it's reference by executive order 14028, treating NIST as authoritative on the topic of Zero Trust is hardly controversial and can help ground a discussion. Accordingly, this post provides a primer on NIST guidance with a focus on the notional Zero Trust architecture first introduced in (SP) 800-207, then practically demonstrated in Implementing A Zero Trust Architecture. It then compares logical components of this conceptual model to a Horizon architecture leveraging the full breadth of Anywhere Workspace Zero Trust capabilities. This should be of interest to anyone looking to enhance windows desktops or applications with Zero Trust security, and, if nothing else, will enable Horizon admins to articulate advancements toward Zero Trust already achieved with their deployments.
A Primer On NIST Zero Trust Guidance
Most descriptions of Zero Trust start by declaring a need to shift from perimeter based network security to a model where hostile actors are always presumed present and within reach. Accordingly, instead of protecting networks the focus is on controlling access to the critical resources themselves through policy based controls that continually evaluate users and their requests. As the abstract for NIST (SP) 800-207 states, “Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.” While this article focusses on guidelines put forth by NIST and NCCoE, I'd like to call out the folksier description of Zero Trust laid out by MobileJon. For most organizations Zero Trust adoption entails a recognition that firewalls and kerberos based security provided by Active Directory no longer cut the mustard given what we know about today's threats.
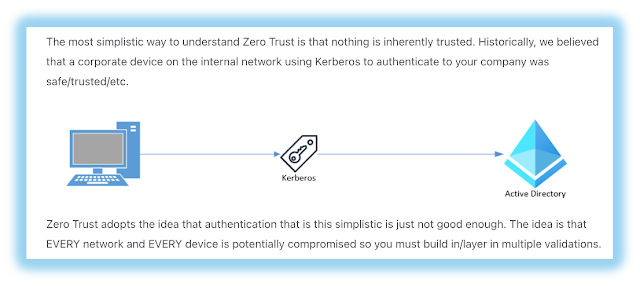 |
| Mobile Jon's Guide To Zero Trust Security |
To replace perimeter based network security (SP) 800-207 introduces a notional architecture detailing logical components required to achieved Zero Trust objectives. In the more recent NIST/NCCoE publication, Implementing A Zero Trust Architecture, example deployments illustrate how commercially available solutions are used to achieve these ZTA objectives. This series of guides, "demonstrate several example ZTA solutions—applied to a conventional, general-purpose enterprise IT infrastructure—that are designed and deployed according to the concepts and tenets documented in NIST Special Publication (SP) 800-207, Zero Trust Architecture." The core functionality driving these ZTA demonstrations is illustrated below:
 |
| Zero Trust Architecture, NIST 802-207 |
To make informed decisions about access requests the Policy Engine processes input from various sources, what are referred to as Policy Information Points (PIP). Data from these sources is ingested into a trust algorithm that determines whether a specific request to a resource should be allowed. Examples of PIPs include endpoint antivirus, endpoint management and security analytics solutions. PIPs contribute to a more comprehensive, 360-degree, contextual model for continually assessing the trust worthiness of a subject. We're not just talking about defense in depth, but rather the coordination and orchestration of various security solutions into a comprehensive model.
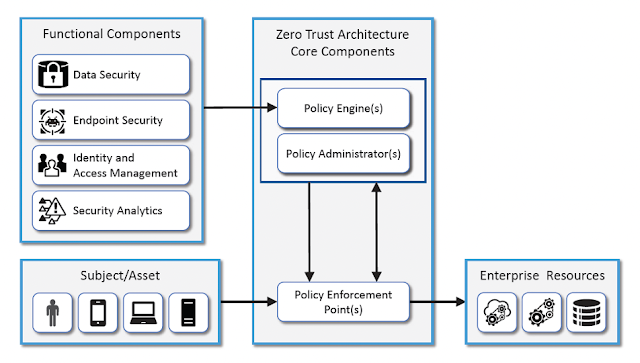 |
| Implementing A Zero Trust Architecture (Fact Sheet) |
 |
| Implementing A Zero Trust Architecture, Volume B: Approach, Architecture and Security Characteristics |
Again, while there's only 5 example architectures today the publication is a work in progress and there's additional examples planned for the future. If I had the option I'd bet large sums of money that VMware products will eventually find their way into future architectures. More conspicuous than the absence of VMware products in the current publication are the listed contributions of VMware employees in 1800-35B. One of these five is Peter Bjork, a very high profile evangelist of VMware's Zero Trust capabilities. While something more exhaustive and definitive might come out in an update to the publication, as a blogger and long time fan of VMware EUC I'm going to take a swag at mapping Horizon and Workspace ONE components to the notional ZTA architecture put forth by NIST.
Mapping VMware EUC Components To A Notional ZTA
To those familiar with VMware's EUC stack the notional ZTA put forth by NIST can come across like a fun adaptation or clever spin on architectures put out by VMware for about a decade. Personally, reading NIST documentation on ZTA felt like deja-vu. (all over again) With it's identity capabilities, federation options and conditional access policies, Workspace ONE Access clearly fits the bill as a policy decision point (PDP), acting both as a policy engine (PE) and policy administrator (PA). These identity based policies for controlling access to resources are further enhanced by solutions like WS1 UEM, WS1 Inteligence and Carbon Black. While these provide relevant security capabilities in their own right, as sources of data providing context for access policies they're clearly acting as policy information points (PIP). Finally, sitting between endpoint devices and virtual desktops on the data plane is Unified Access Gateway acting as a policy enforcement point (PEP).
The ability to drive adaptable authentication requirements through a policy engine has always been a major selling point for WS1 Access. It's conditional access policies for each application are initially defined based on a user's AD membership, general device type, and IP range a request comes from. This contextual insight is extended to device posture through a simple integration with WS1 UEM that incorporates device compliance status into conditional access polices. Historically referred to as, "conditional access based on device compliance," this functionality is achieved through a combination of certificate auth and UEM's device compliance policies. It's an option VMware has offered for about a decade now, functionality foundational to Zero Trust that's mandated by pretty much all sources on ZTA. For example, in BeyondCorp A New Approach to Enterprise Security, a similar approach to incorporating device context is called out, with unique certificates on managed devices used as a conduit to device information. "While the certificate uniquely identifies the device, it does not single-handedly grant access privileges. Instead, it is used as a key to a set of information regarding the device."
Access can also ingest data from Workspace ONE Intelligence regarding device and login risk, further extending the contextual insight of it's policy engine. Both solutions represents the results of analytics run against data collected into the Intelligence data lake from Access or UEM. Device Risk Score is driven by factors like OS patching, anomalous configuration and detected threats on a device. Login Risk Score, "uses machine learning models to analyze past user login patterns and determine if a login attempt is anomalous." Collectively, these risks scores represent additional policy information points to further calibrate our conditional access policies by.
 |
| Setting Up Resources In VMware Workspace ONE Access |
By encapsulating the windows experience into an portable and secure service Horizon provides a catch all solution for extending Zero Trust capabilities to legacy windows apps. Any windows desktop experience or windows app delivered through Horizon can be wrapped in modern auth that's driven by a contextual policy engine. This is no small feat. We're talking legacy applications that rarely support modern auth butting heads with the Zero Trust requirement for extended identity governance. Horizon bridges this gap to meet a fundamental requirement for ZTA. In addition, there's many features of the stand alone Horizon solution, such as Instant Clones, that clearly advance the pursuit of Zero Trust. Non-peristent Horizon models isolate an endpoint device from windows workloads and introduce critical containment that reduces the blast radius of any potential compromise in terms of both space and time. The inherent security awesomeness of Horizon itself and it's contribution to Zero Trust outcomes is something I will detail in a future post.
A Clear Path Forward For Existing Horizon Customers
Existing Horizon customers can progress towards Zero Trust adoption by making incremental improvements to their remote access experience for windows workloads. This fulfills the immediate and practical need to support a hybrid workforce while developing capabilities for Zero Trust adoption across the board. Customers who own Horizon Universal licensing already have the key ingredients for getting started on this journey, Horizon, UAG and WS1 Access. These solutions meet core ZTA requirements and can later be augmented with UEM, Intelligence and Carbon Black. This process of wrapping Zero Trust security around your windows experience is easily adapted to secure SaaS solutions like Office, Salesforce, ServiceNow, Workday or Google Workspace.
Some Excellent VMware Collateral On Zero Trust Adoption
VMware provides some very impressive guidance on Zero Trust, particularly in Tech Zone. In respect to NIST SP 800-207, EO 14028, and their impact on the federal space there's a great article by Andrew Osborn called, Incorporating VMware Zero-Trust For the Presidential Executive Order. It offers a summary of cybersecurity mandates and models created to guide federal agencies in their adoption of Zero Trust. These include CISA's Cloud Security Technical Reference Model and Zero Trust Maturity Model. At the end of the article Andrew states, "VMware will be augmenting our solution alignment and future whitepapers to incorporate the new CISA foundational pillars."
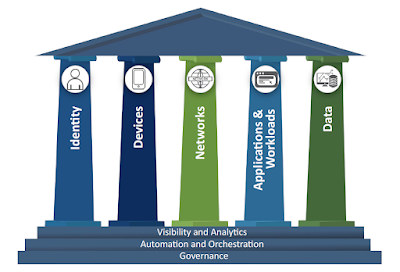 |
| Zero Trust Maturity Model 2.0 |
True to this promise is one of my favorite articles on Zero Trust and Horizon, Zero Trust Secure Access to Traditional Applications with VMware. It provides a very thorough and exhaustive account of how different capabilities across the Anywhere Workspace stack can contribute to a Zero Trust architecture for legacy windows applications. It organizes these capabilities according to 5 pillars of trust. They might look familiar to you.
Conclusion








This comment has been removed by a blog administrator.
ReplyDelete