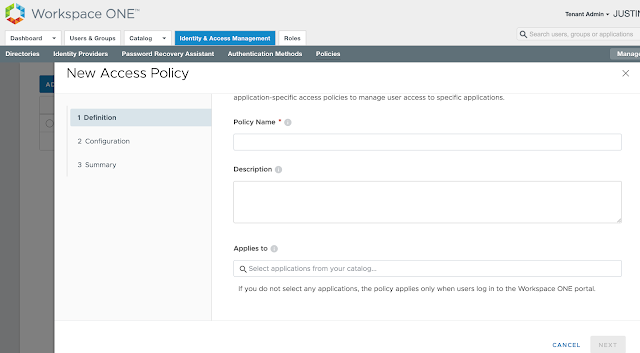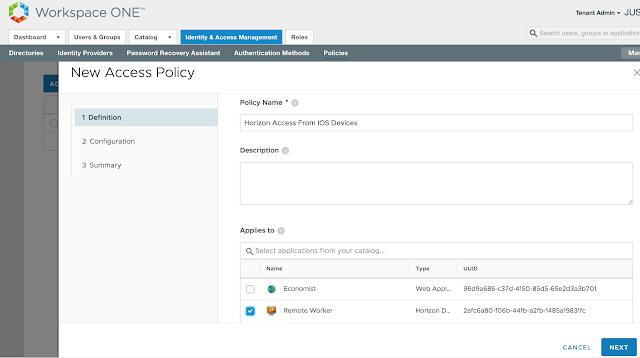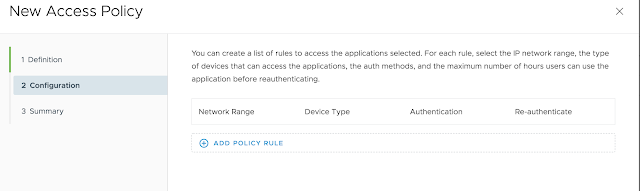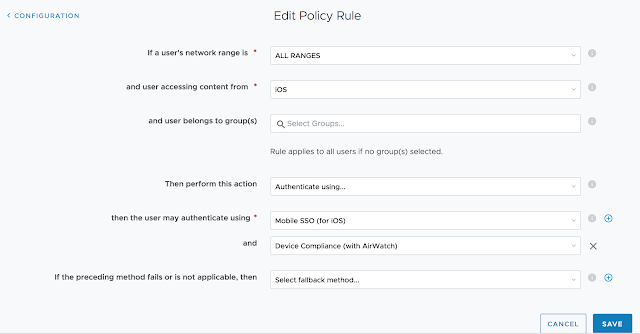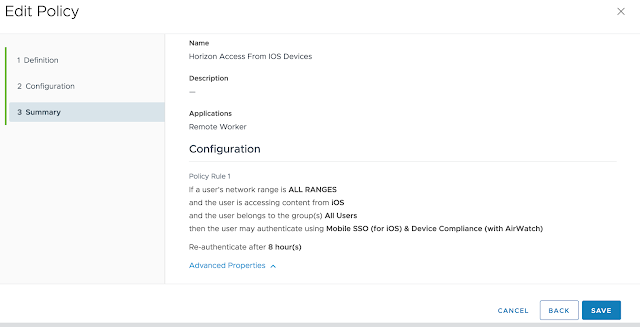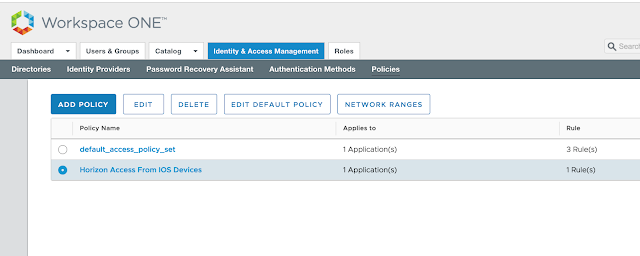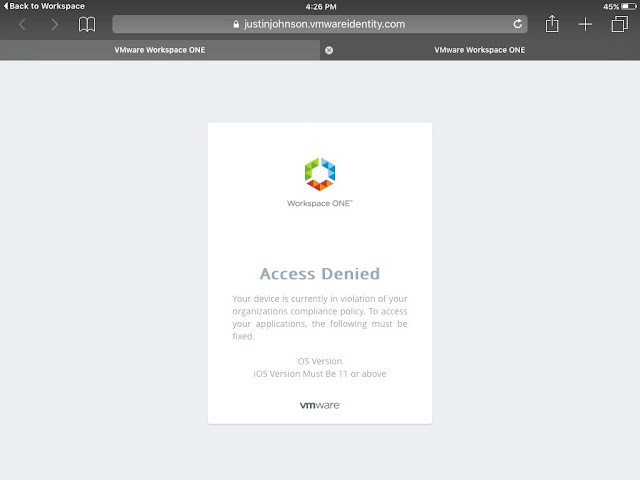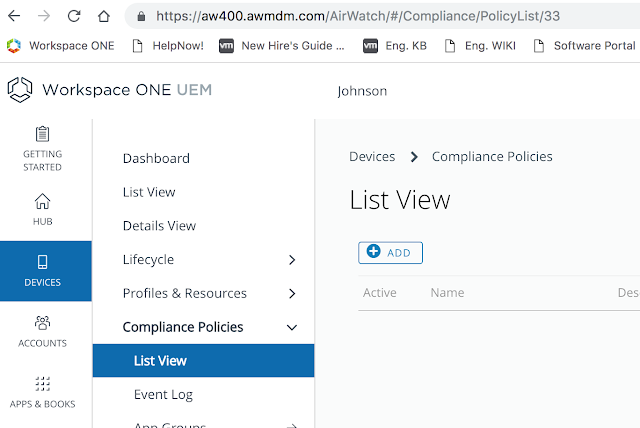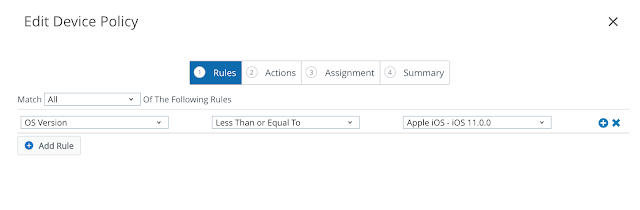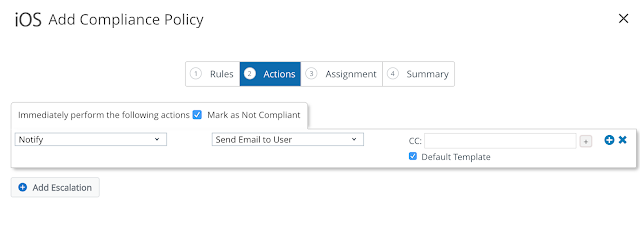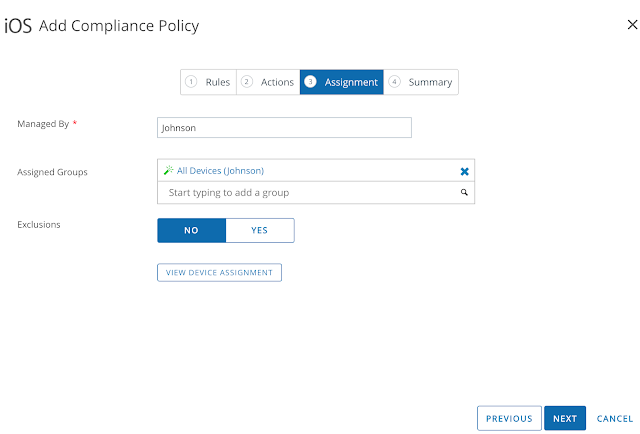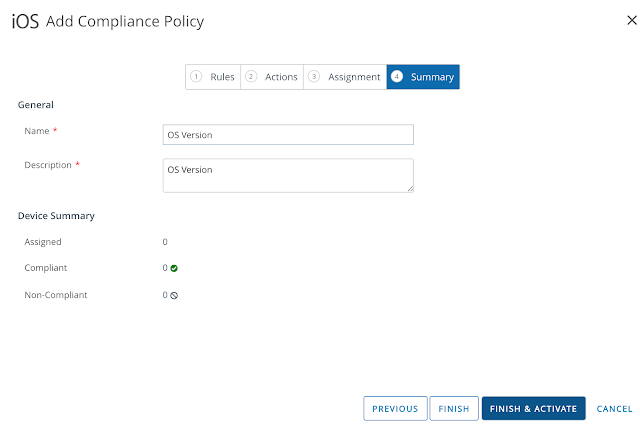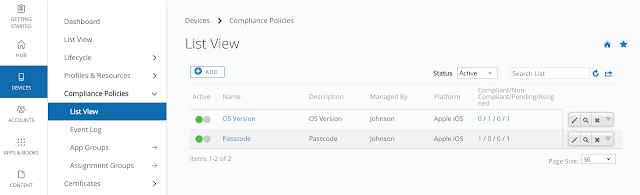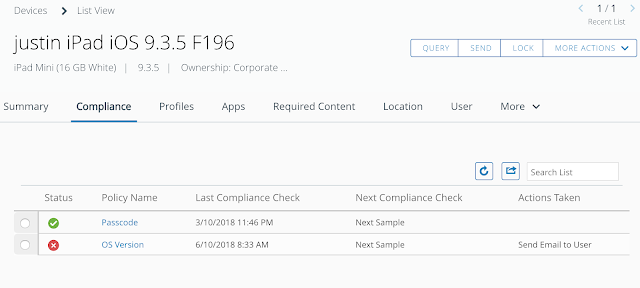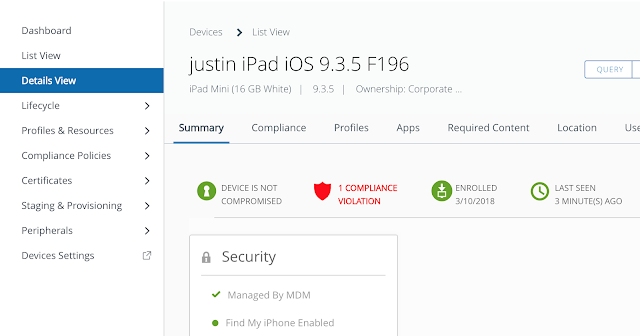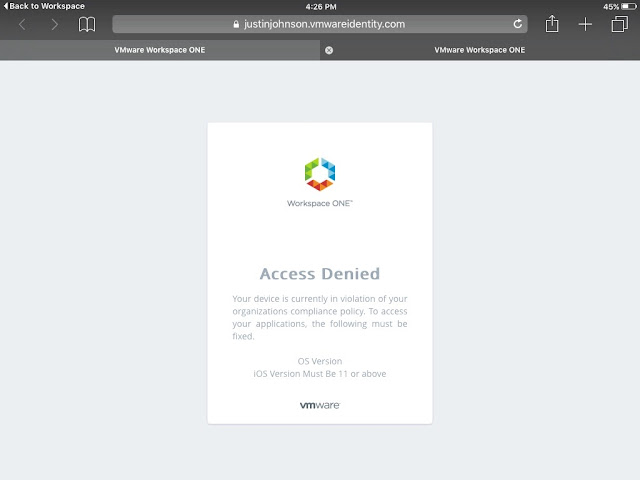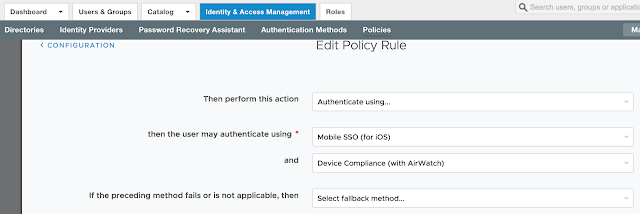
Long story short, we need to get Mobile SSO for iOS setup and configured properly before we can take advantage of device dompliance as an authentication method. To achieve this, we're first going to enable the built in certificate authority for AirWatch. Then we'll enable and configure the Mobile SSO for iOS authentication method. Next, we'll associate this authentication method with the new built-in IDM we're going to create. Finally, we'll push out required identity provider settings onto the target devices using a special iOS profile.
Enable AirWatch Certificate Authority
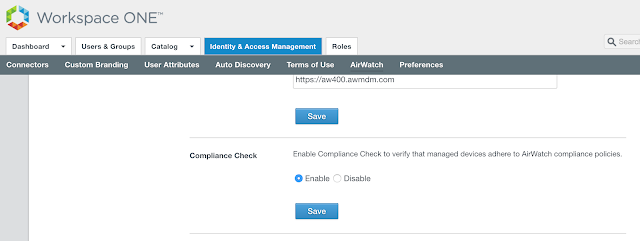
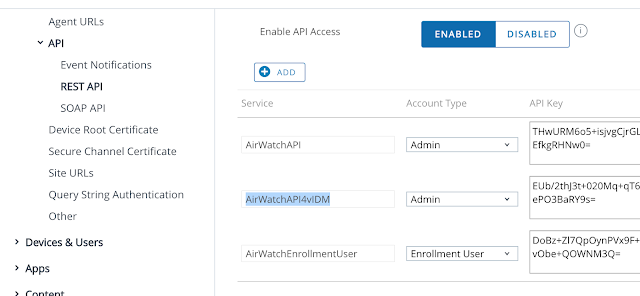
While there's the option to use a Microsoft Certificate Authority, the path of least resistance is to leverage the built in certificate authority AirWatch can provide. To enable it, navigate to Groups And Settings --> All Settings --> System --> Enterprise Integration --> VMware Identity --> Configuration. Click on the enable button for Certificate Provisioning.
After enabling certificate provisioning you'll see some info about the issuer certificate populated on the screen.
Click the export button for the Issuer Certificate. You'll need this certificate to configure the Mobile SSO for iOS authentication method in vIDM.
Configuring The Mobile SSO (for iOS) Authentication Method
In the vIDM admin console, navigate to Identity & Access Management --> Manage --> Authentication Methods. Click the pencil for Mobile SSO (for iOS).
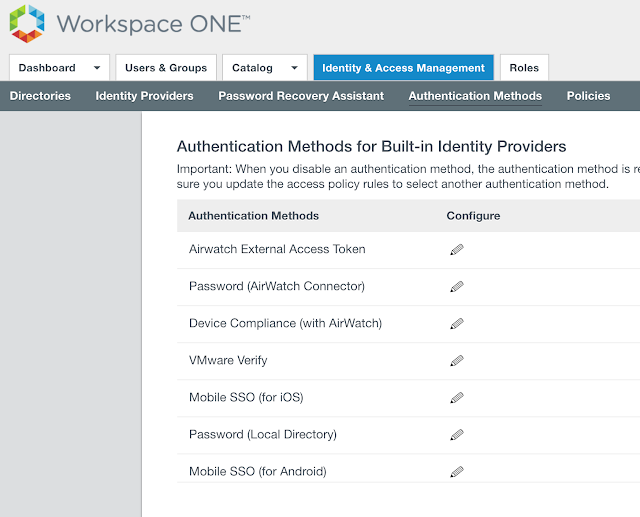
You want to check the box for, "Enable KDC Authentication."
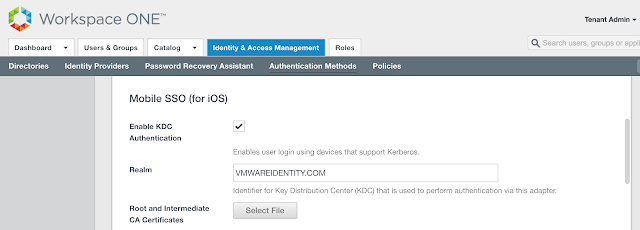
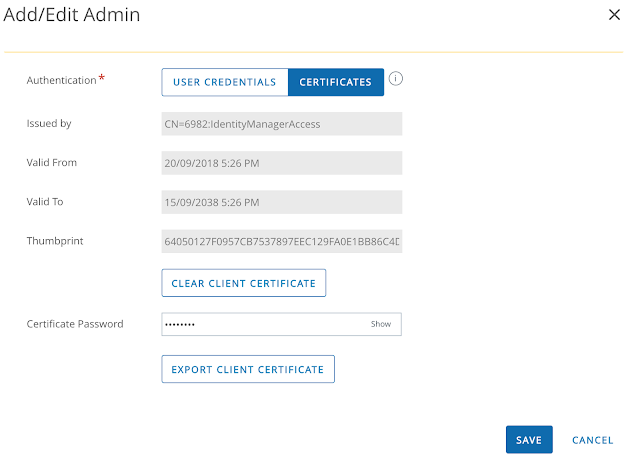
The realm will be automatically populated. Next, click on the Select File button to upload the issuer certificate we just exported from AirWatch.

You want to check the box for, "Enable KDC Authentication."

The realm will be automatically populated. Next, click on the Select File button to upload the issuer certificate we just exported from AirWatch.
Navigate to the certificate.
Click okay to confirm and upload the file.
After a successful upload you'll see info about the certificate populate on the screen.
Also, for a reason I can't explain, the device compliance authentication method wouldn't work for me till I unchecked the option for, "Enable OCSP," and, "Send OCSP Nonce." Don't ask me why it was breaking things. All I know is that while googling an error message and following the suggestion of disabling OCSP in the following post, I was up and running:
https://communities.vmware.com/thread/547237
https://communities.vmware.com/thread/547237
Finally, click save. You'll get a pop up message that the adapter has been updated.
Create A Built-in IDM And Associate It With Mobile SSO For iOS
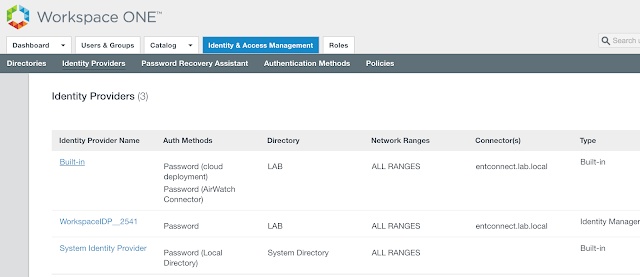
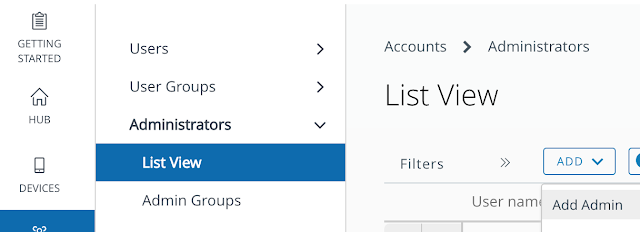
Navigate to Identity & Access Management --> Mange --> Identity Providers. Click on Add Identity Provider and select the option for, "Create Built-in IDP."
Give it a fun name and select the appropriate directories and network ranges.
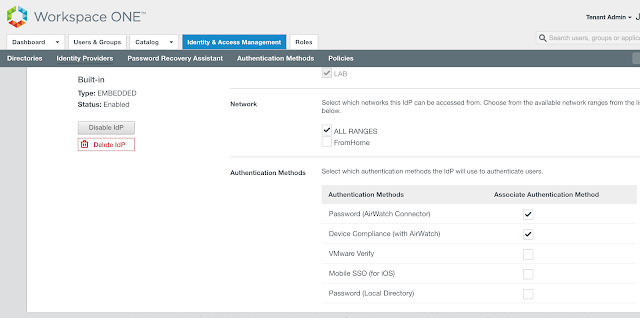
Under Authentication Methods check the options for Device Compliance (with AirWatch) and Mobile SSO (for iOS). Finally, click Add.
Now, when you navigate back to the newly created provider there's an option to download the certificate. Download the certificate. This cert will get pushed out to your iOS device by means of a device profile.
Creating An Apple iOS Profile To Push Out Identity Provider Settings To Your Devices
You'll create an iOS profile in AirWatch to push out vIDM settings to your endpoint devices. Navigate to Devices --> Profiles & Resources --> Profile. Click on Add Profile.
Select iOS as the profile type.
Name the profile iOSKerberos.
Scroll down to SCEP and click on configure.
From the drop down menu select AirWatch Certificate Authority for both the credential source and certificate authority. Select Single Sign-On for the certificate template.
Scroll down to Credentials an select configure.
Navigate to the KDC certificate you just exported from the identity provider.
Info about the cert will get populated on the screen.
Finally, scroll down to Single Sign-On. Click on the configure button.
For the account name enter in Kerberos. For the Kerberos Principal Name, click + and select {EnrollmentUser}. For the realm name, enter in the realm name of your tenant. (Most likely VMWAREIDENTITY.COM.) Under renewal certificate, I went with SCEP #1. For URL Prefixes, enter in the full name of your tenant.
Scroll down a bit. Then for an application identifier, add com.apple.mobilesafari.
Next, publish and assign this new profile to the target endpoints. Once the profile applied to the endpoint, you can confirm it's been applied by going to Settings --> General --> Device Management --> Device Manger.
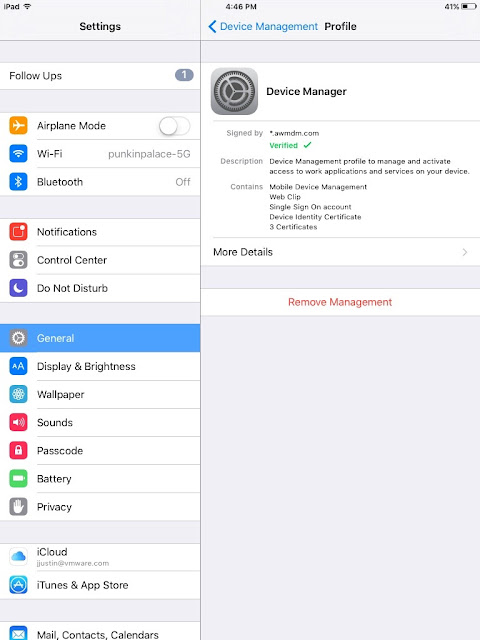
Click on more details. You'll see among other things, the kerberos settings included in the profile.
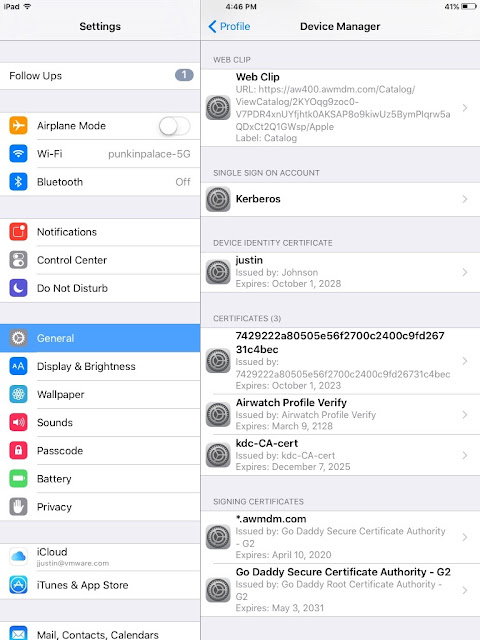
Click on Kerberos and you can actually see some of the specific settings you just configured.
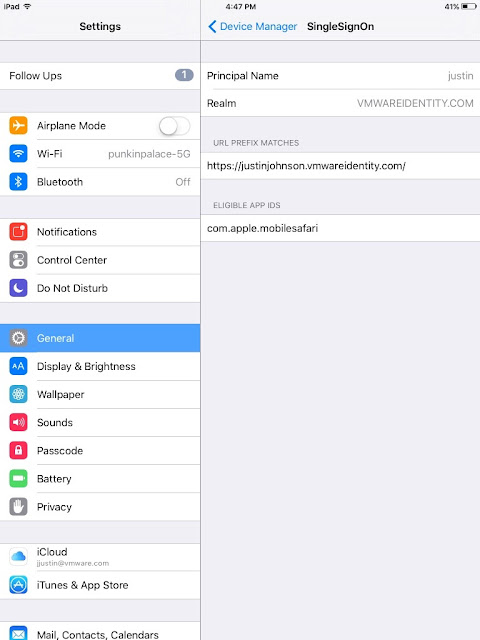

Click on more details. You'll see among other things, the kerberos settings included in the profile.

Click on Kerberos and you can actually see some of the specific settings you just configured.

At this point, the configuration of Mobile SSO for iOS is complete. We can proceed to enable device compliance as an authentication method. For guidance, check out this next post, Securing Access To Horizon Through AirWatch Based Device Compliance.