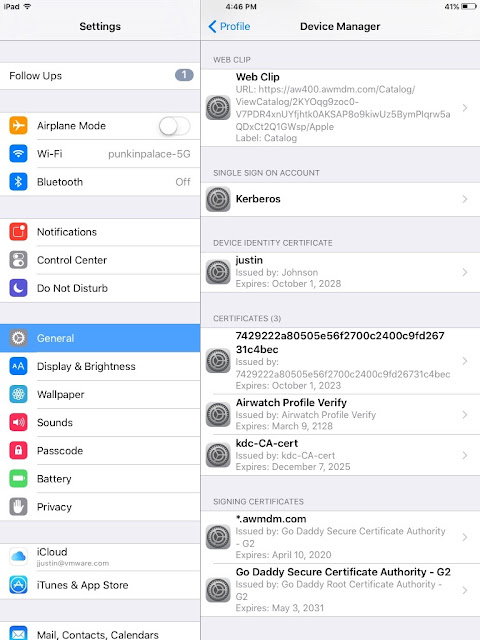
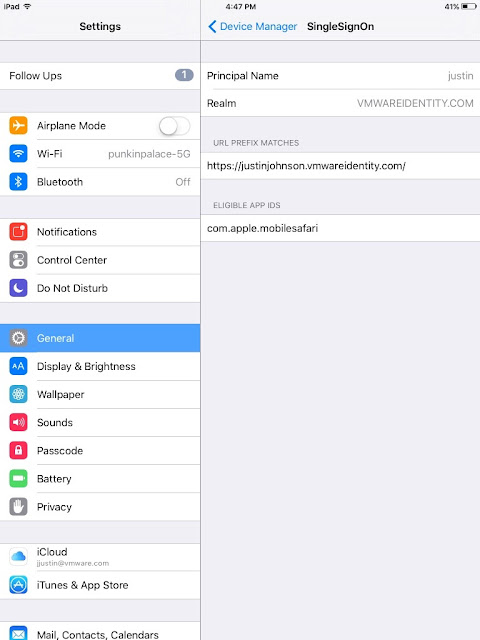
Intelligent Hub has full feature parity with the former AirWatch agent. For pure Workspace One UEM (AirWatch) deployments there's no real difference aside from the name changing and rebranding. However, the new catalog functionality it offers introduces dependencies not previously required by the Workspace One App it's intended to replace. To provide catalog services from Intelligent Hub you need to configure Hub Services ahead of time. These Hub Services are co-located in VMware Identity Manager cloud-hosted environment and are an absolute requirement if you want to provide an app catalog directly from the Intelligent Hub app.
As a cranky techie that hates change, initially I was a bit put off by this new app. The prospect of a migration from the Workspace One app to Intelligent Hub was intimidating, especially given the new dependencies. However, there's a couple pieces of good news that really mitigated my concerns. First, the configuration of Hub services isn't exactly rocket science. Configuring Hub Services within my Workspace One lab environment, one that already had vIDM and Workspace One UEM fully integrated, was for the most part straight forward and uneventful. Second, the Intelligent Hub app, even with it's Hub Catalog enabled, can run side by side with the Workspace One App on the same device. So you can configure and enable Hub Catalog on endpoint devices, but can postpone an actual migration from the Workspace One App till a more convenient and opportune time for you users.
Given these 2 pieces of good news, and the promise of a better more interactive service that Hub Catalog can offer, there's only a few reasons why you wouldn't proceed with the configuration of Hub Services and publishing of the Hub Catalog:
Unfortunately, Hub Catalog isn't currently supported for on premise implementations of vIDM and only works with vIDM cloud-hosted. So customers using on premise vIDM for a Workspace One deployment should continue using the Workspace One App for catalog services. The same goes for folks using a 9.x version of Workspace One UEM (AirWatch). They can continue to use the Workspace One App app as well. Otherwise, for folks who'd like to take the Hub Catalog for a test spin, here's the steps I followed to enable the Hub Catalog in my own lab environment.
Relax, It's Not That Bad A Situation For Workspace One Admins
As a cranky techie that hates change, initially I was a bit put off by this new app. The prospect of a migration from the Workspace One app to Intelligent Hub was intimidating, especially given the new dependencies. However, there's a couple pieces of good news that really mitigated my concerns. First, the configuration of Hub services isn't exactly rocket science. Configuring Hub Services within my Workspace One lab environment, one that already had vIDM and Workspace One UEM fully integrated, was for the most part straight forward and uneventful. Second, the Intelligent Hub app, even with it's Hub Catalog enabled, can run side by side with the Workspace One App on the same device. So you can configure and enable Hub Catalog on endpoint devices, but can postpone an actual migration from the Workspace One App till a more convenient and opportune time for you users.
Given these 2 pieces of good news, and the promise of a better more interactive service that Hub Catalog can offer, there's only a few reasons why you wouldn't proceed with the configuration of Hub Services and publishing of the Hub Catalog:
- You have an on premise instance of vIDM
- You're using a Workspace One UEM version below 1810
- You're attached to the Workspace One App for sentimental reasons
- The possible future deprecation of the Workspace One App is a reflection of your own mortality and you don't have time for an existential crisis
Unfortunately, Hub Catalog isn't currently supported for on premise implementations of vIDM and only works with vIDM cloud-hosted. So customers using on premise vIDM for a Workspace One deployment should continue using the Workspace One App for catalog services. The same goes for folks using a 9.x version of Workspace One UEM (AirWatch). They can continue to use the Workspace One App app as well. Otherwise, for folks who'd like to take the Hub Catalog for a test spin, here's the steps I followed to enable the Hub Catalog in my own lab environment.
Enabling Hub App Catalog
Both the Workspace One UEM and vIDM include links to Hub Configuration. Within the Workspace One UEM console, it can be access from Groups & Settings --> Hub Configuration. On this initial Hub Configuration page, I entered in my vIDM tenant URL and then clicked Launch.

At the customization page, I accepted the defaults.
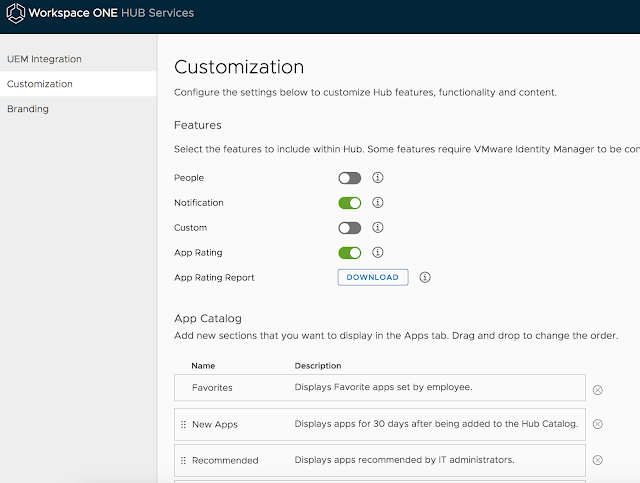
Then I clicked save.
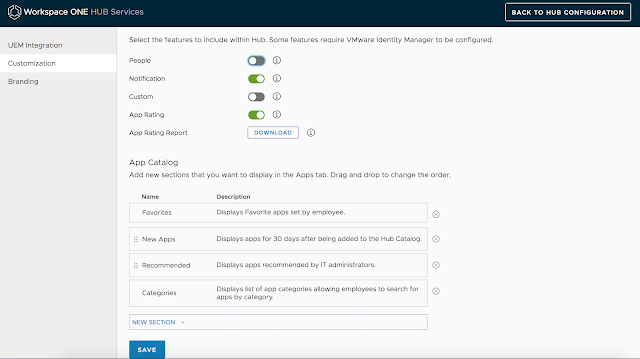
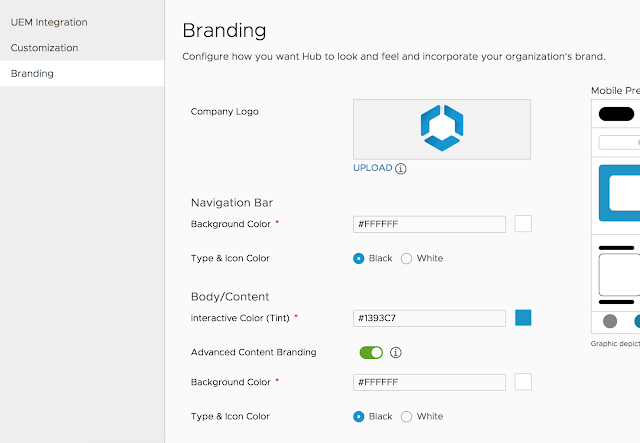
Next, I accepted the defaults for branding and clicked save.
Phhhhheeeeeeeeewwwwww!!!!!! Tired yet? Well dig deep and push just a little harder. We still have a few buttons to push.
Setting The Source Authentication For Intelligent Hub To Identity Manager
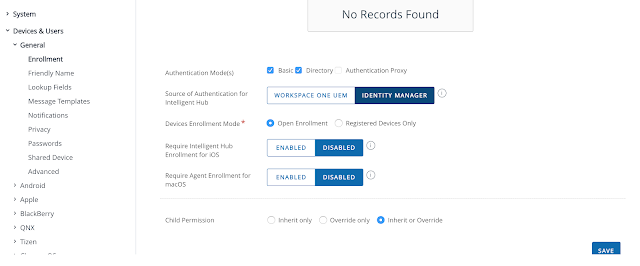
The official guidance indicates that when fully integrating Hub Services with vIDM, you need to select Identity Manager as the source of authentication for Intelligent Hub. Accordingly, I navigated to Devices > Devices Settings > Devices & Users > General > Enrollment, then selected Identity Manager authentication manager as the source of authentication for Hub and clicked save.
Publishing The Hub Catalog
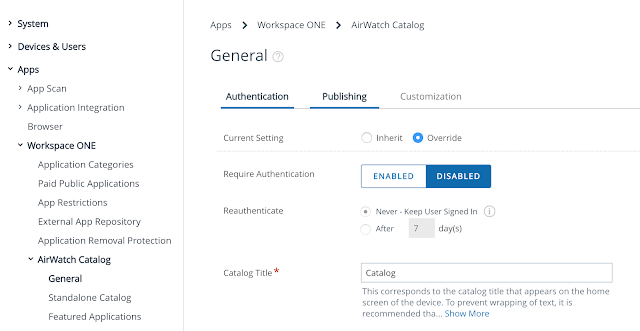
Finally, I had to publish the Hub Catalog for iOS. To do that, I navigated to Groups & Settings > All settings > Apps > Workspace ONE > AirWatch Catalog > General.
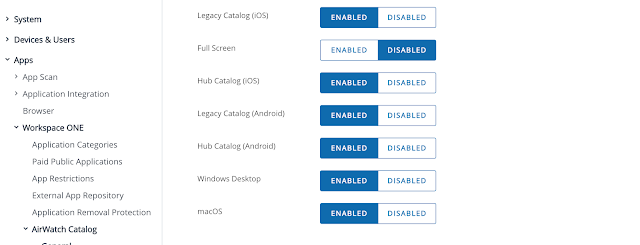
Then I clicked override, enabled Hub Catalog (iOS) and clicked save.
After performing the steps above, Hub Catalog was displayed after loading up the Intelligent Hub from the home screen. On the first screen, I could seen, among my favorites my virtual desktop entitlement:

I also found the self service catalog for the provisioning of mobile apps I'd been entitled to.
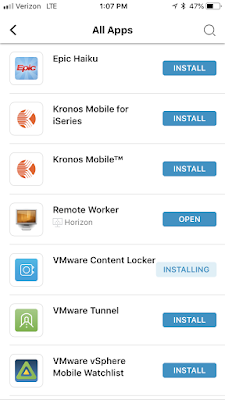
Running Both Catalogs Side By Side
As I previously mentioned, configuring Hub Services wasn't exactly rocket science, which takes the edge off making this transition. Further, there's the fact that both catalogs can theoretically exist side side on the same device, which means you can enable the Hub Catalog on users devices without having to force an immediate transition away from the Workspace One app. Here's a video demonstration of the Hub Catalog and Workspace One App catalog functioning from the same device: