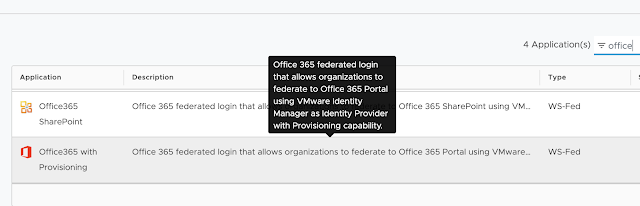
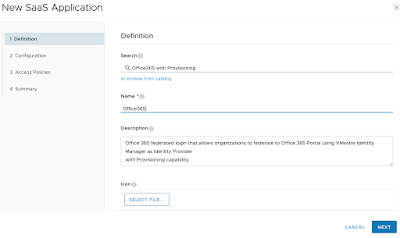
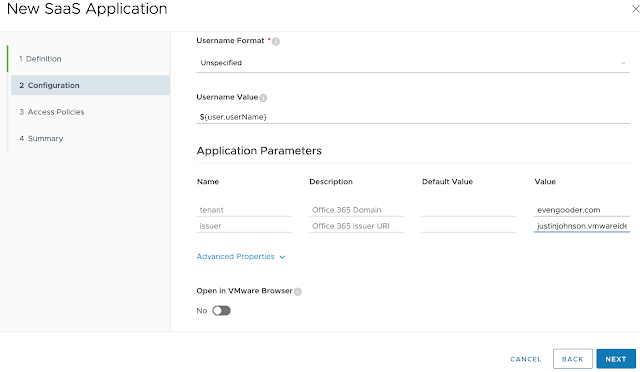
In my first desktop support role I’d hop from cubicle to cubicle, hurling my plastic Microsoft Office 2000 disk like a ninja star at beige Dell towers. I’d take a seat at a users desk, pop in my little silver friend, punch in a memorized CD key and then, 10 to 15 minutes later, I’d assure the user it was no problem at all and walk on to the next cubicle.

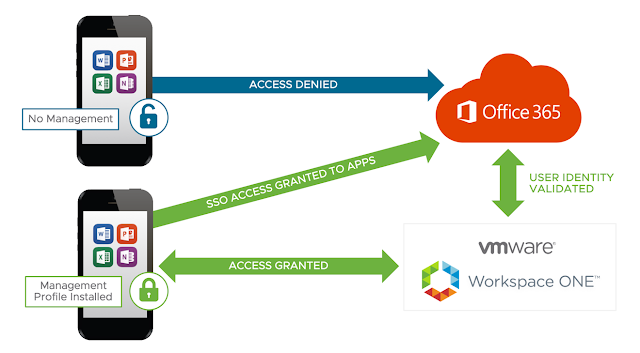
Well, it’s 2019 and everything’s more demanding and complex. With Office 365 deployments we're aiming to make Office available to users from anywhere on pretty much any mobile device. To fulfill this desire for ubiquitous Office access, engineers must design for a balance between convenience and security. To think such a task will be easy or without challenges is about as reasonable as this:

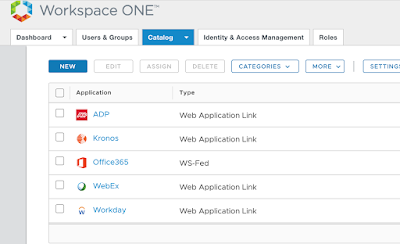
After the challenge of securing Office 365 is truly appreciated the Workspace ONE solution becomes and incredibly compelling proposition. Leveraging cloud based instances of Workspace ONE Access and UEM, within hours we can wrap WS1 security and convenience around Office 365 access. Not only does this address Office 365 deployment challenges, but it also establishes a foundation for the delivery of other SaaS based solutions within a digital workspace.
Recipe Overview
The Standard Microsoft Options For Office 365 Access
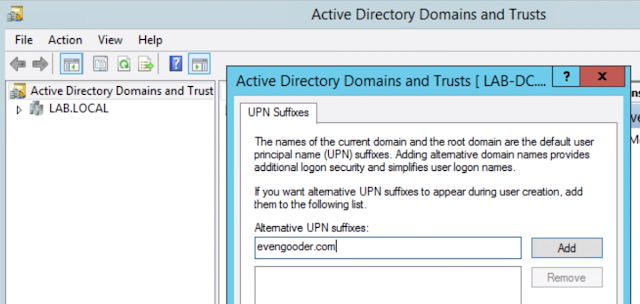
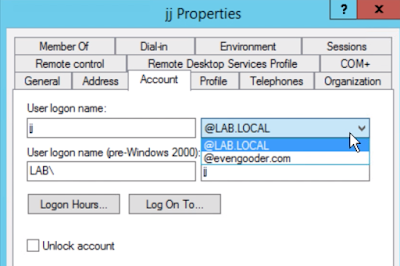
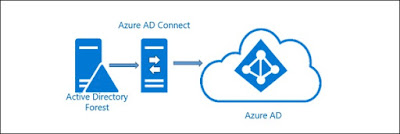
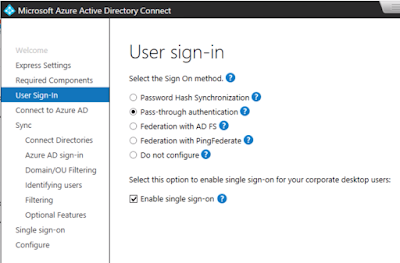
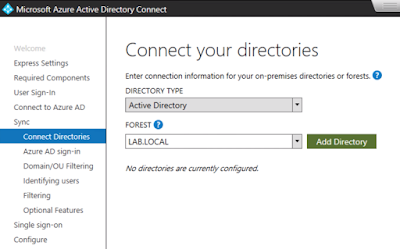
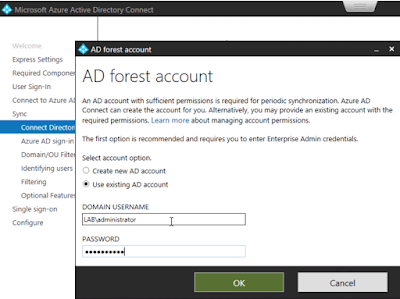
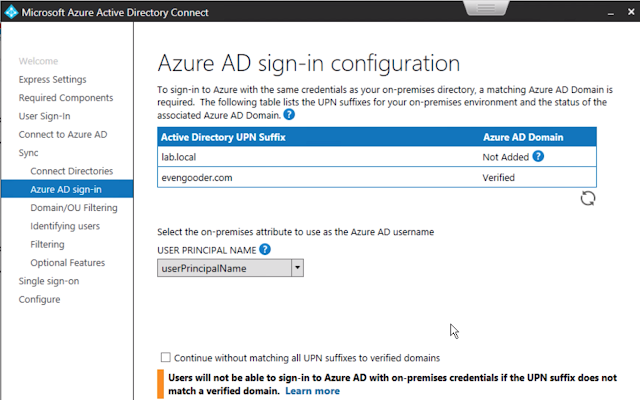
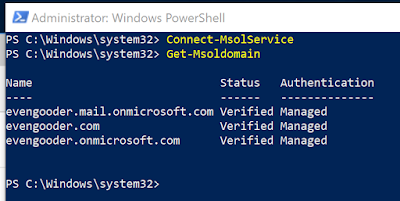
If you want to leverage local AD accounts for Office 365 access you start by standing up an instance of Azure AD Connector within your trusted network. This component syncs your local AD users to your Azure tenant, which in turn allows you to entitle them to office 365 licenses. Once these users are synchronized and enabled for Office 365 access, the next question is, "how do you authenticate these users against the local AD environment. For that you have 3 basic options: ADFS, PHS (Password Hash Synchronization), and PTA (Pass-through Authentication).
Password Hash Synchronization
Password hash synchronization is the default authentication method when Azure AD Connect is installed. One of the more notable features of this option is that you don't need to pol any holes in any firewalls or setup any internet accessible infrastructure. Local AD passwords, via the Azure AD Connector, are hashed and stored in the Azure environment so that AD users can authenticate to Office 365 using their normal credentials.

Pass-through Authentication
Similar to PHS, Pass-Through Authentication (PTA) allows you to authenticate against your on-premises AD environment without having to poke holes through firewalls or setup any internet accessible infrastructure. However, no AD password are hashed in your Azure environment. Instead, authentication against your local AD environment is handled by a special agent running on Azure AD Connect within your trusted environment. This agent communicates with the Azure tenant over outbound 443 traffic.

Seamless Single Sign-On
Regardless of whether you go with PHS or PTA, you can leverage seamless single sign-on for your on premise users. This capability makes PHS or PTA a very attractive option for replacing ADFS in situations where Office 365 is the only application you need access to.

ADFS
ADFS is the original Microsoft solution for addressing authentication of on-premises AD users to Office 365. Unlike PHS or PTA, if you want users to have access to Office from the external world, with the ADFS model you'll need to setup some internet facing infrastructure. In light of this requirement, PHS or PTA appear to be the path of least resistance. However, if you're looking to integrate other SaaS solutions outside of Office, without the assistance of any other 3rd party IDPs, ADFS is still relevant.
Utilizing Workspace ONE Access For Office 365
Workspace ONE Access Federation With ADFS
One option for integrating Workspace ONE with Office 365 involves federation with ADFS. ADFS is federated with Azure, and then in turn is federated with Workspace ONE Access. This can involve setting up Workspace One Access as a 3rd party identity provider for ADFS or vis versa, configuring ADFS as 3rd party identity provider for Workspace One Access.
Workspace ONE Federation With Another 3rd Party Identity Solution
Another option is to have some kind of federation between your Office 365 environment and another identity provider like Ping or Okta. Then in turn, you can federate the 3rd party IDP with Workspace ONE access, allowing the 3rd party IDP to leverage the device awareness of Workspace ONE UEM.
Direct Federation Between Azure And Workspace ONE Access
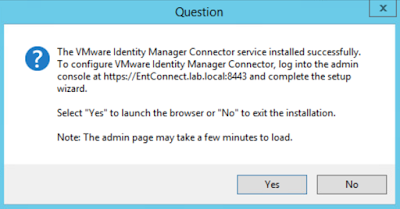
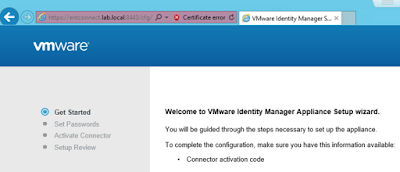
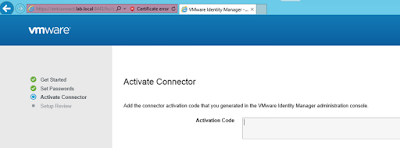
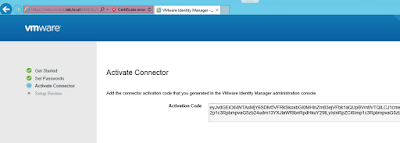
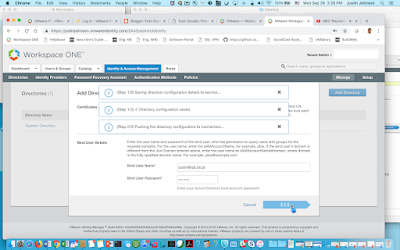
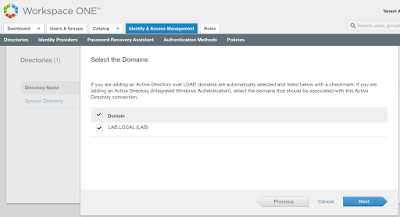
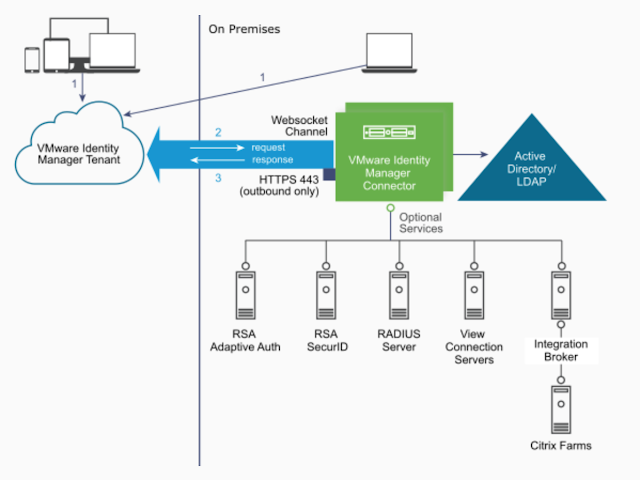
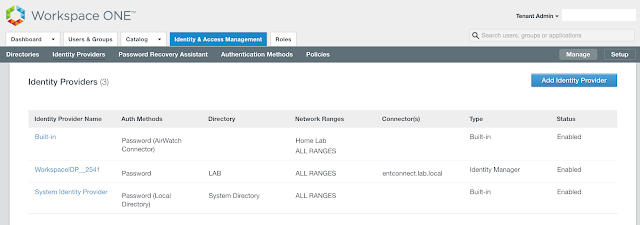
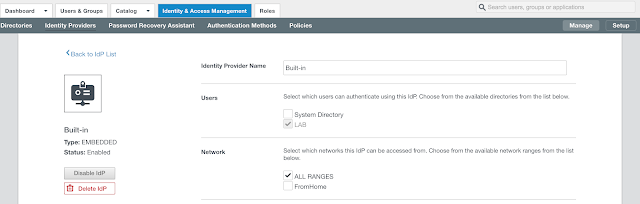
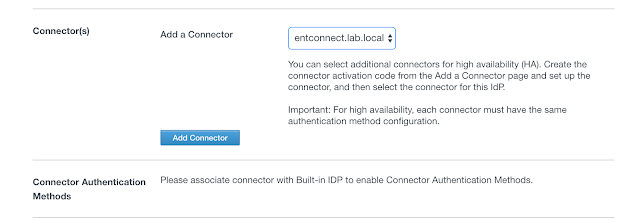
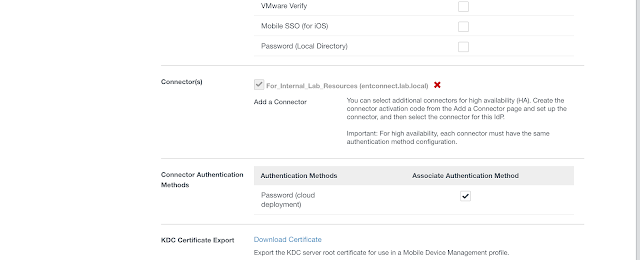
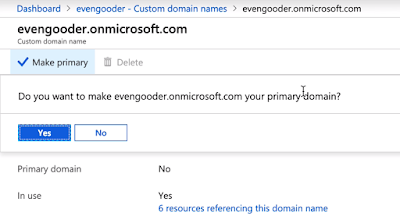
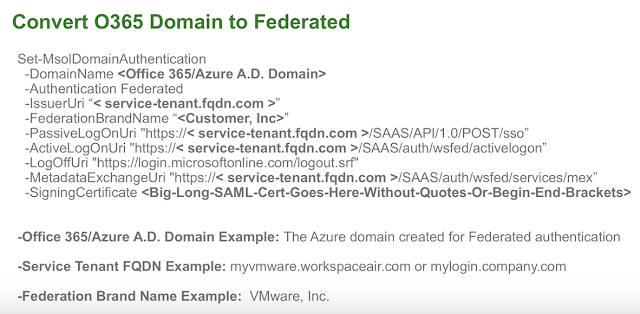
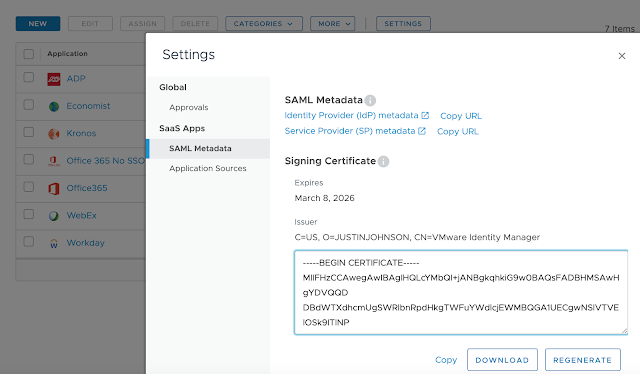
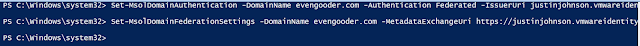
The recipe detailed in my post, Wrapping Workspace ONE Goodness Around Office 365 - A Quick Dirty Recipe, is based on a direct federation between Workspace ONE Access and an Azure tenant. With this model, Workspace One Access becomes the primary identity provider for your Office 365 subscription. A key capability that allows for this is configuring an on premise vIDM Connector in outbound mode. While Azure AD Connect continues to sync users to the Azure tenant, actual authentication is handled by a vIDM Connector in a manner very similar to Microsoft's Pass-Through Authentication model.

The benefit of this deployment model is the simplicity of setting up PTA combined with the full breath of Workspace ONE capabilities. Most notably, we get the benefits of an integration with Workspace One UEM (The artist formerly know as AirWatch.) Leveraging the device compliance policies of WS1 UEM (AirWAtch), we can factor in device posture when implementing our conditional access policies.

Additional Resources
Wrapping Workspace ONE Goodness Around Office 365 - A Quick And Dirty Recipe:
https://www.evengooder.com/2019/09/WS1-Goodness-Arround-Office365-Quick-n-Dirty.html
Hybrid Identity And Directory Synchronization For Office 365:
https://docs.microsoft.com/en-us/office365/enterprise/plan-for-directory-synchronization
Official VMware Guidance:
https://www.vmware.com/pdf/vidm-office365-saml.pdf
Dean Flaming Elaboration:
https://m.youtube.com/watch?t=1s&v=fUSTdsGk6ko&noapp=1&client=mv-google
Peter Bjork Blog:
https://blogs.vmware.com/horizontech/2016/12/vmware-identity-manager-2-8-office-365-user-provisioning-federation.html
Preparing a non-routable domain for directory synchronization:
https://docs.microsoft.com/en-us/office365/enterprise/prepare-a-non-routable-domain-for-directory-synchronization
Configuring VMware Identity Manager As A Third Party IDP In AD FS:
https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/vidm-configuring-vidm-in-adfs.pdf
VMware Identity Manager using Azure AD as 3rd party Identity Provider:
https://blogs.vmware.com/horizontech/2016/12/vmware-identity-manager-using-azure-ad-3rd-party-identity-provider.html