With the steps detailed in my previous posts complete, we can begin to leverage AirWatch device compliance for conditional access. Using this authentication method you can mandate device compliance in AirWatch as a prerequisite for access to an application. In this post, access to a Horizon desktop pool is going to be restricted to devices that are not only AirWatch enrolled, but also compliant according to AirWatch compliance policies. For guidance on the prerequisites for enabling this feature, see this previous post. Otherwise, follow the steps below to enable device compliance as an authentication method in vIDM.
Enabling Device Compliance
Within the vIDM console, navigate to Identity & Access Management --> Setup --> AirWatch.
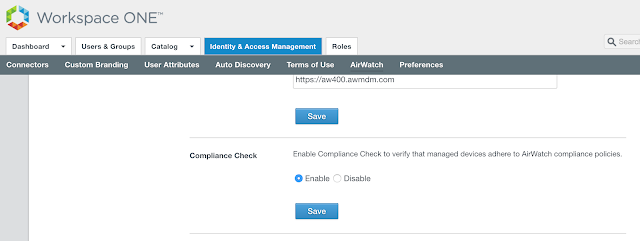
Scroll down to Compliance Check. Select enable and click save.
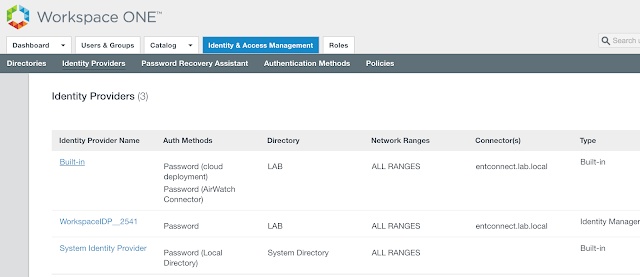
Next, to leverage device compliance as an authentication requirement within vIDM access policies it needs to be enabled as an authentication method within the Built-in identity provider. To do so, navigate to Identity & Access Management --> Manage --> Identity Providers. Click on the hyperlink for Built-in.
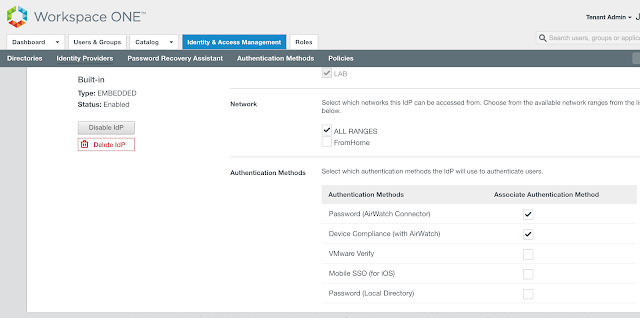
From there, scroll down to authentication methods and check the box for, "Device Compliance (with AirWatch)." Then scroll down further and hit save.
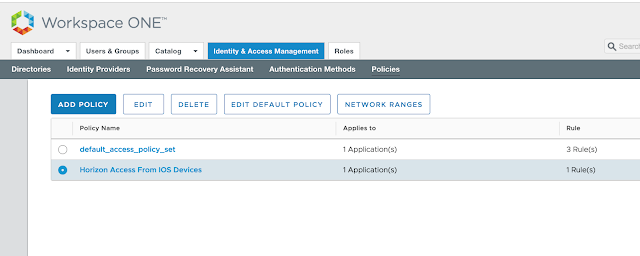
At this point, "Device Compliance (with AirWatch)," will show up as an option under access policies.
Mandate Device Compliance For Horizon Access
We can now make AirWatch device compliance a prerequisite for Horizon access through the creation of an access policy in vIDM. Within the vIDM management console, navigate to Identity & Access Management --> Manage --> Policies.
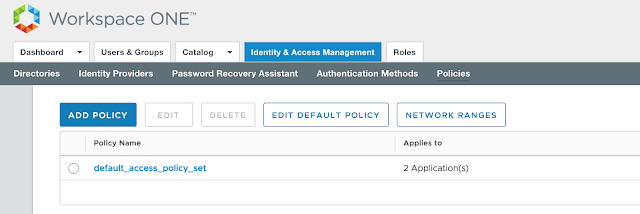
Click the Add Policy option.
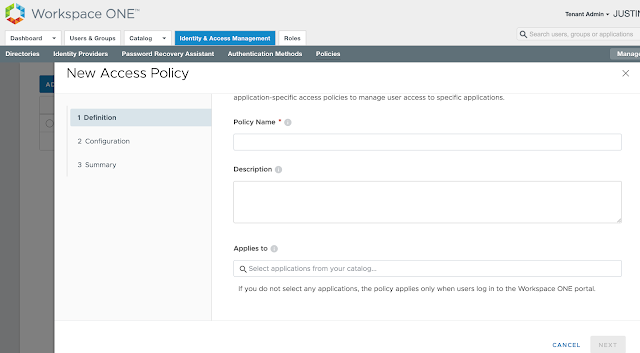
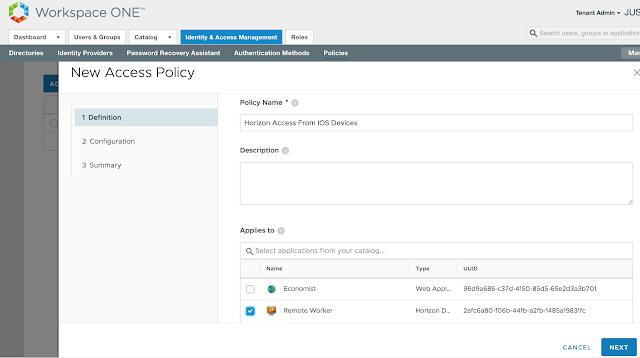
Provide a descriptive name for the policy and select the relevant Horizon entitlement.
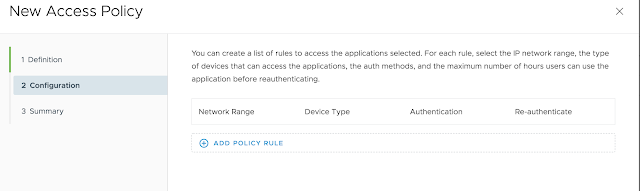
Next, under configuration, select, "Add Policy Rule."
 Pick a network range for this new rule as well as applicable device type. For this test, I'm going to select ALL Network ranges and iOS. Then, for authentication requirements I'm going to select both, "Mobile SSO (for iOS)," and, "Device Compliance (with AirWatch)."
Pick a network range for this new rule as well as applicable device type. For this test, I'm going to select ALL Network ranges and iOS. Then, for authentication requirements I'm going to select both, "Mobile SSO (for iOS)," and, "Device Compliance (with AirWatch)." 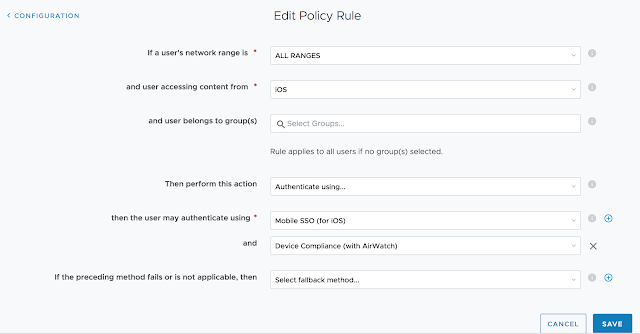
This mandates that folks trying to access this Horizon desktop pool from an iOS device must have an AirWatch compliant device.
Confirm the summary information and hit save.
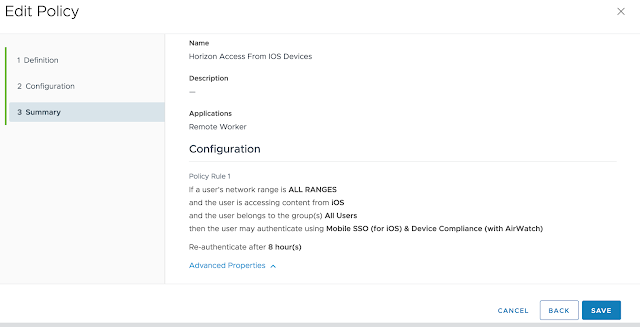
You'll see your new access policy show up under policies.
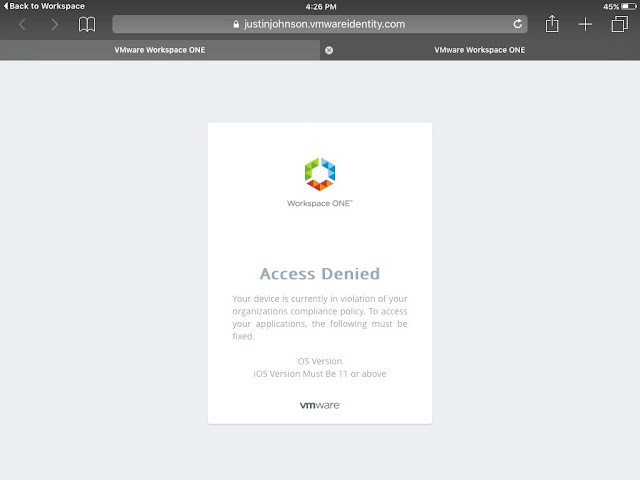
With this policy in place folks who try to launch the Remote Worker Horizon desktop pool from iOS devices won't be granted access unless their device is compliant according to defined compliance policies in AirWatch. If they're endpoint isn't compliant, they'll get a message like this when trying to launch the virtual desktop.
Creating A Compliance Policy In AirWatch
To test device compliance for Workspace One delivered applications we need to enable a test compliance policy within AirWatch. From the AirWatch console, navigate to Devices --> Compliance Policies --> List View. Click on the Add button.
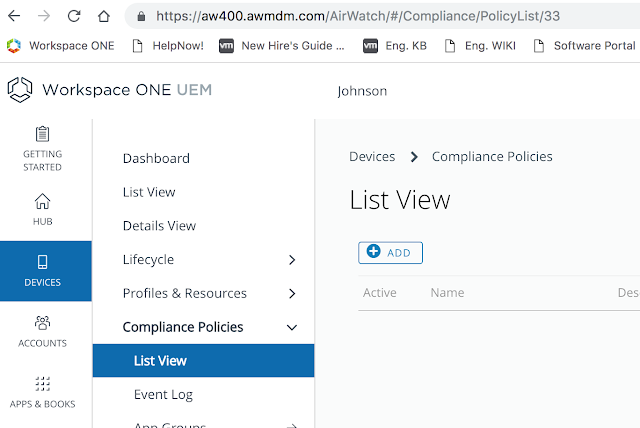
Since I'm testing against an iPad device I'm going to create a compliance policy for iOS.

For the sake of testing, I'm going to create a policy that's sure to mark my iPad as noncompliant, one that flags devices that are below iOS 11. (My iPad is 9.35.)
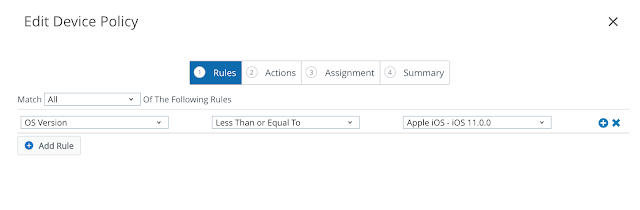
For actions, I'm just going go with notify. In real life, you'd probably get a little more involved than that.
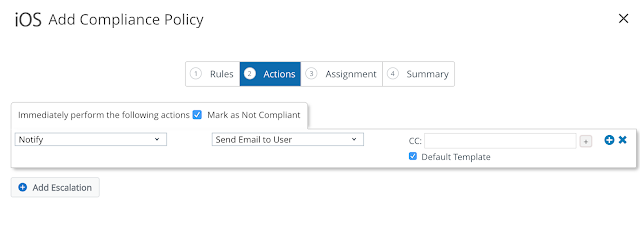
Again, for testing, I'll just apply this policy to all devices.
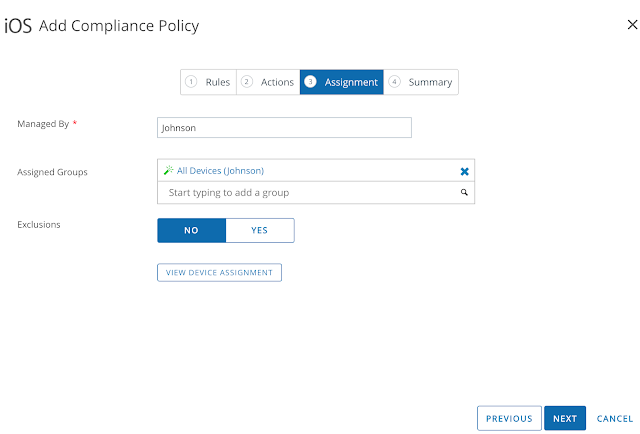
Finally, after reviewing the summary, click Finish & Activate.
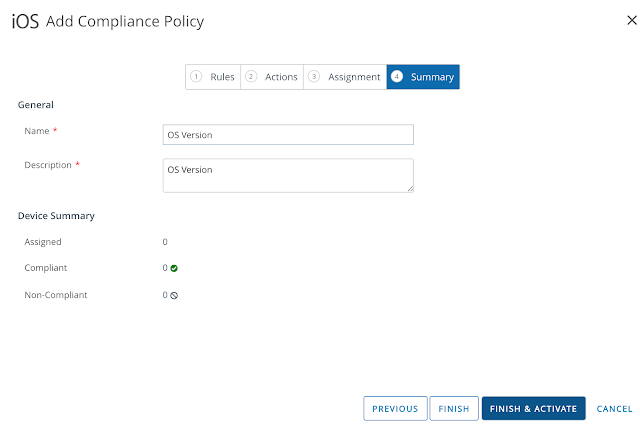
At this point the newly created policy shows up under the list view for Compliance Policies.
Once this policy gets evaluated it's status shows up as red under my devices Compliance tab.
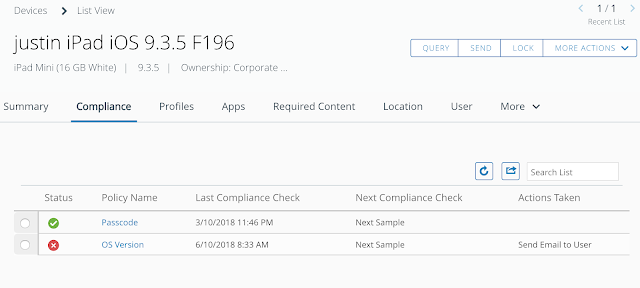
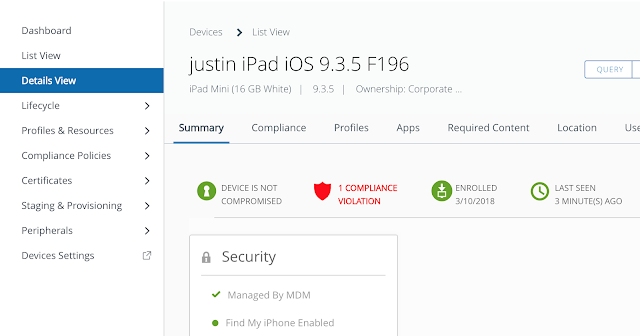
And the device is reported as having a compliance violation.
At this point, if I try to access my Remote User Horizon desktop pool, I get the error:
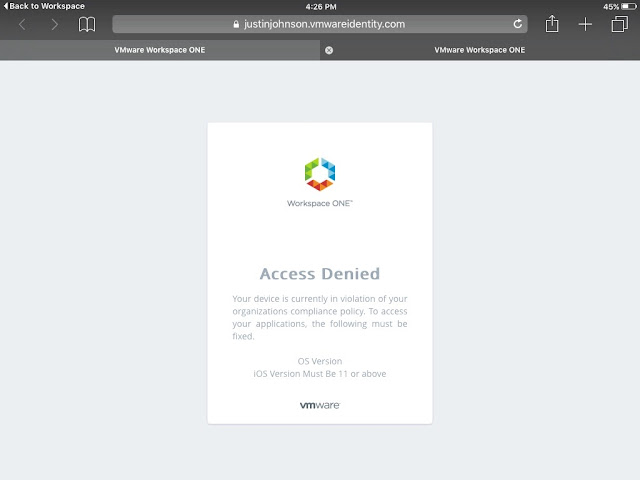
Not only do we get an explanation for why access is denied, but we also get the name of the violated policy and it's description. Theoretically, in the real world, a user would go on to upgrade the device in order to be complaint. For testing, you can just remove the OS Version compliance policy from the endpoint and the device will go from non compliant to compliant. At that point, access to the virtual desktop will work as expected.
I have this configured and can authenticate via the browser going to my WorkSpace One Access address. However, I can't seem to get my app configuration correct. Can you document how to configure an app? I have the bundle ID set in my profile, but the app does not do any URL redirection, currently it points at our internal SSO, should it point at the new WorkSpace One Access portal instead?
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDelete