Recently I helped integrate Horizon 7.2 with Symantec VIP 9.8 to provide RADIUS authentication for Horizon Apps. The ultimate goal was to provide 2 factor authentication for remote connections coming through a UAG appliance in the DMZ. While UAG 3.0 can integrate directly with a RADIUS server, we discovered we could provide 2FA THROUGH the UAG 3.0 appliance via a direct integration between the Symantec VIP Enterprise Gateway and our Horizon Connection server. The whole setup looks something like this:
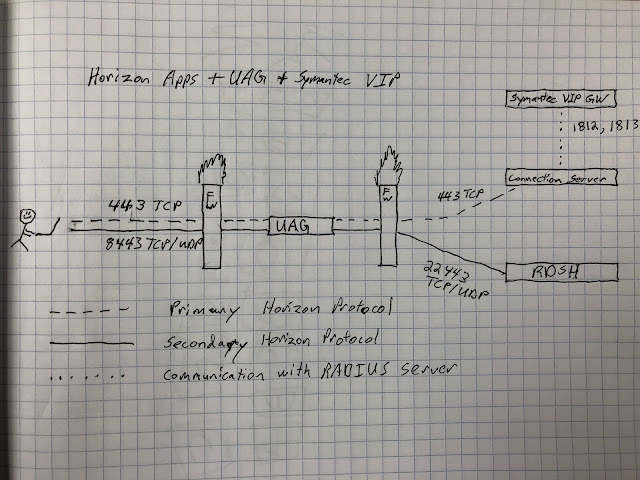
As you can tell from the incredibly professional drawing above choosing to integrate directly with the Connection server spared us the creation of additional firewall rules. Further, it provided us a well traveled path to Symantec VIP integration. Support for RADIUS started with View 5.1 and includes a long list of vendors. Plenty of folks have done it over the years. In regard to Symantec VIP in particular, an integration guide called the Symantec VIP Integration Guide for VMware was put out in 2012. Most of what this guide details still holds true today. Below is an excellent graphic from the guide that illustrates the gist of how the integration works.
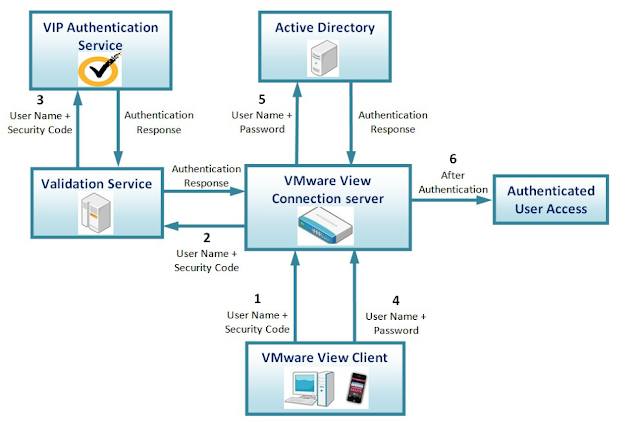
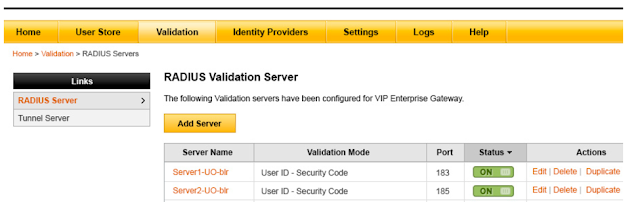
Now this guide was put out 5 years ago and details the integration between Horizon 5.1 and Symantec VIP 8.x. Translating it for todays use involves working through a few changes in terminology. First, in current Symantec documentation "authentication modes" are referred to as “validation modes.” 2nd, whereas the original guide says to setup the Symantec validation server in “User Name + Security Code,” mode, the modern equivalent of this in Symantec 9.8 is “User ID – Security Code.” Once you account for this updated terminology, the process for integrating with Symantec VIP is the same as it was when the guide was put out 5 years ago. Here's a sample screenshot of a Symantec VIP Enterprise Gateway Validation Server properly setup to provide radius authentication for a Horizon environment. (For more info on how to setup the Symantec VIP Enterprise Gateway, check out this install and config guide.)

As you can tell from the incredibly professional drawing above choosing to integrate directly with the Connection server spared us the creation of additional firewall rules. Further, it provided us a well traveled path to Symantec VIP integration. Support for RADIUS started with View 5.1 and includes a long list of vendors. Plenty of folks have done it over the years. In regard to Symantec VIP in particular, an integration guide called the Symantec VIP Integration Guide for VMware was put out in 2012. Most of what this guide details still holds true today. Below is an excellent graphic from the guide that illustrates the gist of how the integration works.


With a validation server setup properly the next step is to configure the Horizon Connection server itself. So navigate to View Configuration > Servers > Connection servers. Select the connection server you want to enable 2 factor authentication and navigate to it's authentication tab. Select RADIUS for your two factor authentication option and select, "Create New Authenticator."
The process for creating the authenticator is identical to that detailed in the integration guide. Here's a sample of what it looks like today:
Finally, select this new authenticator and check the box, "Enforce 2-factor and Windows user name matching."
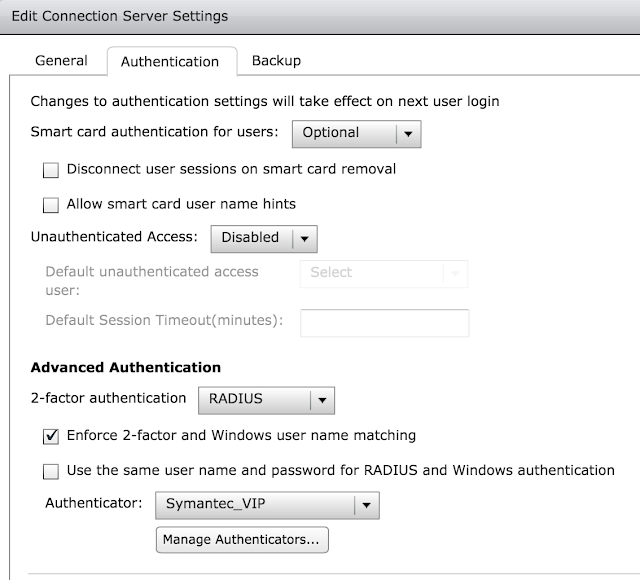

At this point you should be all set. When authenticating to this Connection server - whether directly or through the UAG appliance - you'll first get prompted for your passcode, then your normal AD credentials.


No comments:
Post a Comment